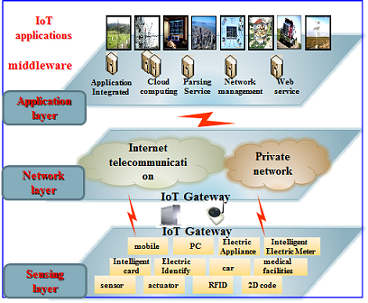
Every enterprise will be affected by the benefits and challenges that Internet of Things (IoT), the growing phenomenon by which not only people, but also “things” — vehicles, commercial and industrial equipment, medical devices, remote sensors in natural environments — are linked to networks that are connected to the internet. The profound impact on businesses and the business value it brings will to a large extent be dependent upon overcoming the overwhelming Cybersecurity challenges that characterize the phenomenon of connecting “Things” in the Internet. IoT senses and identifies the physical world via sensing technology and intelligent devices, performs computations, processing and knowledge mining through networking, realizes interaction between people and things, things and things, achieves real time control of the physical world, precise management, and scientific decision makings.
The application of IoT extends to manufacturing, logistics and retail sectors, energy and utilities sectors, intelligent transportation systems, environment monitoring systems, home management and monitoring, etc.
Advances in IoT development have been remarkable in all forms and shade. Despite this, the adoption of IoT has been slowed down by security concerns. In January, 2014, an Infonetics research revealed that security concerns topped the list of barriers to IoT adoption with 58%. Regulatory compliance came a distance second with52%. While it is generally accepted that in the coming years IoT will integrate into most enterprise businesses with varying business values, there is also a general agreement that IoT represents a growing enterprise threat that will require developing new standards, governance, risk management and compliance and security controls in IoT Ecosystem within an International Policy Framework. But, there are significant challenges in fashioning a framework that addresses the myriad of IoT implementation requirements. The challenges for enterprises lie in identifying where security controls are needed – and then designing them to be responsive to emerging IoT Cyber security threats.
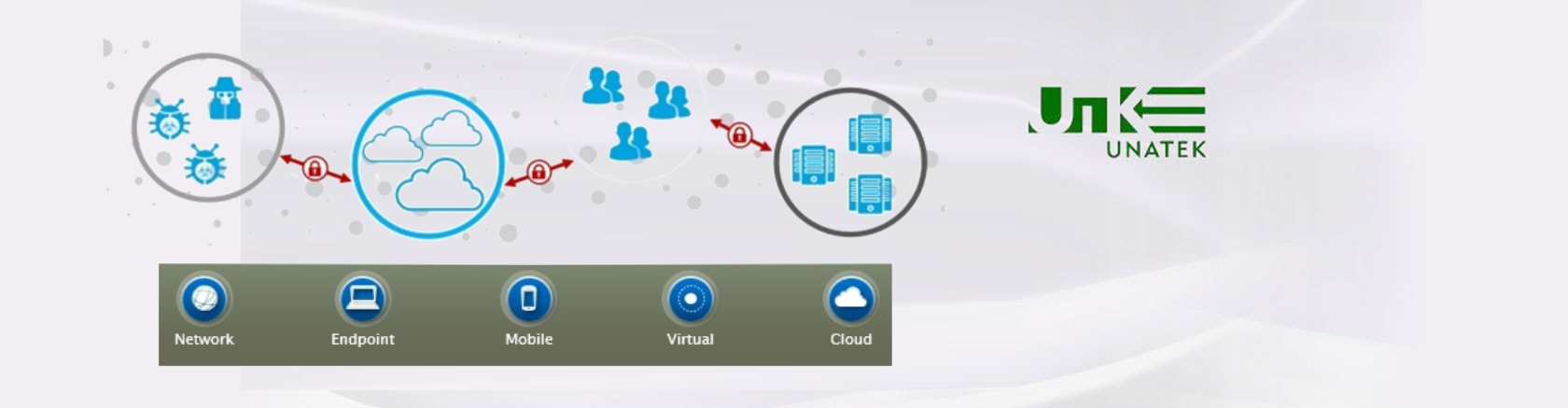
The Cyber security design for an IoT environment is different from the design in today’s organizational networks. Why is it different? The IoT architecture, design and underpinnings are different from those of today’s network:
- The deluge of IoT data and “Things” requires a different set of privacy and security controls
- The nature of disruption and denial-of-service attacks that on IoT-based devices are different
- known Internet vulnerabilities are more complex and manifest in different forms for IoT
- Vulnerability Management for IoT imposes a different set of requirements
- The new set of technologies, hardware and software components that are not part of today’s Internet infrastructure require a different set of security mechanisms
- Bandwidth demand requirements are huge and rapid in IoT deployments
- IoT event transportation and communication modes are different from today’s enterprise network transport
- IoT devices and applications are vast, very diverse and complex from both IT and infrastructure standpoints that requires fashioning new standards, frameworks to meet their Cyber security needs
The implication is that Cyber security requirements are inherently distinctive for integrating IoT capabilities and requires deployment of a new set of security controls with new risk management strategies, new network security evaluation tools, and revisions in operational security strategies.
In practical terms, for security and privacy assurance of enterprise IoT deployment, an organization’s tasks are to (i) deploy IoT security technology, (ii) implement IoT safety and security assurance system, and (iii) integrate IoT network infrastructure safety.
IoT security technology
- Delineate the requirements, develop the architecture, design the basic security structure of IoT, develop information collection, transmission, processing and application common technologies specific to the IoT capability being introduced
- Implement privacy protection, device/node authentication, access control, cryptographic key management, infrastructure routing security, intrusion detection and fault tolerance measures
IoT safety & system security assurance
- Develop a risk management plan built around NIST and ISO frameworks as well as other government regulatory compliance requirement specific to the particular IoT. The plan should include establishment of third party compliance verification security testing system established as a notification mechanism to assess the security risk and system reliability
- Establish a system of IoT security risk and system Reliability Evaluation
- Implement an SDLC program and interoperability for the sustenance of the planning, design, operation and maintenance of the IoT total life cycle
- Establish service level agreements for outsourced IoT project or application development to assure IoT application security, risk management and system reliability assurance
IoT network infrastructure safety
- Design secure integration architecture for the secure integration of IoT devices and applications into existing network architecture. This will assure full integration of existing resources with the new technology application reserve space, realize the smooth and compatible conversion of old and new technologies, and assure the security and safety of IoT infrastructure
A good starting point would be to review emerging frameworks within the public domain and then selectively implement those that align with the Cyber security requirements of the IoT deployment environment. The Cloud Security Alliance has proposed an initial set of security controls that can be referenced to deploy or integrating IoT capabilities or products in an organization.
- Analyze privacy impacts to stakeholders and adopt a Privacy-by-design approach to IoT development and deployment
- Apply a Secure Systems Engineering approach to architecting and deploying a new IoT SoS
- Adopt a data-centric approach to the security of IoT systems
- Implement layered security protections to defend IoT assets
- Implement device-specific protections for IoT assets
- Define Life-cycle controls for IoT devices
- Define and implement an IoT asset management approach
- Define and implement an authentication/authorization framework for the Organization’s IoT Deployments
- Define and implement a Logging/audit framework for the Organization’s IoT ecosystem
- Develop safeguards to assure the availability of IoT-based systems and data
- Information Sharing, supporting a global approach to combating security threats by sharing threat information with security vendors, industry peers and Cloud Security Alliance